Download — https://urloso.com/2nk2h2
Download — https://urloso.com/2nk2h2
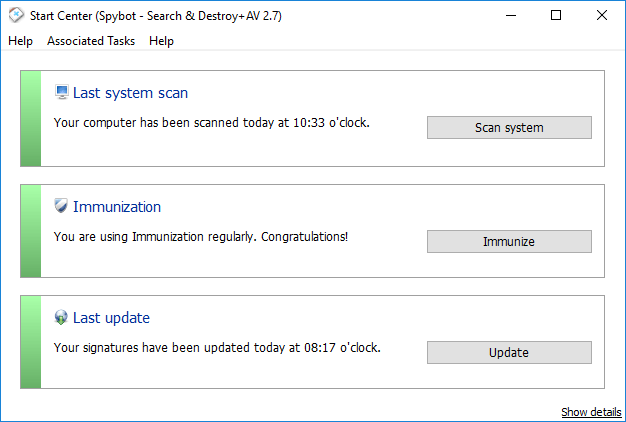
HACK Spybot – Search Destroy 1.6.0.30
Spybot – Search & Destroy can detect and remove various types of spyware from your computer.n Spyware is a relatively new type of threat .n and search and destroying it securely protects your computer.
These powerful tools scan suspicious files in Windows, user lists, registry and other suspicious areas of the system and leave you only files that are safe to use.
Chapter 9. Basic Concepts of Internet Intrusion Protection
The Internet is a completely open environment and you can make various forms of illegal intrusion into it from the network. Many people face various forms of illegal attacks.
Known types of illegal Internet intrusions include spam, phishing, web spam, and other types of fraud. To protect your computer from illegal Internet penetration, you must use these basic Internet concepts.
1. Spam
Spam is one of the most common types of illegal intrusions. Spammers are spreading malicious content on your computer system and these are the sites you should be focusing your attention on. Non-governmental organizations, government agencies, the media, criminals, and others may also send spam.Spam can be avoided by using filters.
Send unwanted emails to the trash and move on to another part of this document.
2. Phishing
Phishing is a type of illegal interference in a computer network, the purpose of which is to obtain confidential data for fraudulent purposes. The purpose of phishing is to get people to click on a link that leads to a page containing fraudulent data or simply unnecessary information. You can easily find many sites offering to disclose confidential information or simply post a link on the Internet. Phishers can use a variety of techniques to corrupt your computer and get you hooked.
Take steps to protect against phishing. Turn off the Internet on your computer while doing research. If you are using a network printer, make sure it is set to print documents on odd days. Always check your inbox and never send emails without making sure you open each email to the end. If you have access to IP addresses on many computers, always add one IP address using the ipconfig command. You can also limit the overall traffic by configuring the protocols.
3. Web spam
WebC
3e8ec1a487
https://intrendnews.com/all-in-one-keylogger-4-0-top-cracked/
http://www.wellbeingactivity.com/2022/06/09/ant-man-english-telugu-movie-free-download-2021-mp4/
https://bootycallswag.com/2022/06/09/marshall-mathers-lp-2000-download-zip/
https://setewindowblinds.com/cimatron-e9-full/
https://xiricompany.com/human-psychology-books-in-malayalam-pdf-74/
http://thetruckerbook.com/2022/06/09/stoneloops-of-jurassica-juego-spanis-hack-torrent/
https://visitfrance.travel/a_profile_of_france/pedeset-nijansi-sive-pdf-scribd-free/
https://wilsonvillecommunitysharing.org/blur-game-english-language-pack-patcher-free/
https://www.onlineusaclassified.com/advert/best-seo-company-in-noida-seo-services-agency-in-noida/
https://www.iltossicoindipendente.it/2022/06/09/copy-file-bin-tanaka-t21/
https://www.chimfab.com/gamze-ozcelik-gokhan-demirkol-videosu-link/
https://wakelet.com/wake/t7Kdjn7_zun1BtMhgflnU
http://dottoriitaliani.it/ultime-notizie/bellezza/man-of-the-xpose-full-movie-in-hindi-download-1080p-hd-free/
http://festivaldelamor.org/?p=5027631
http://mulfiya.com/windows-7-sp1-x64-12-in-1-by-adguard-august-updated-os4world-utorrent/
https://embeff.com/arma-armed-assault-crack-1-04/
https://yellowtagbyvike.com/vedam-telugu-movie-in-hindi-dubbed-free-download/
https://thenationalcolleges.org/?p=5801
http://viabestbuy.co/full-maktaba-shamila-16000-free-download-full-version-download/
https://thebrothers.cl/soft-computing-book-by-sivanandam-pdf-free-verified-17/





































